SEARCH ARTICLES
Cybersecurity Skilled Labor Shortage
Alȳn Inc. has successfully provided value added Cybersecurity services to the Federal Government and Fortune 50 for over 10 years. With this experience and our battle-hardened, dedicated Cybersecurity expertise, we are expanding into the Commercial Sector. Through industry research and [...]
Building Blocks for a Successful Cybersecurity Strategy
Building a successful Cybersecurity strategy is not complicated but is essential to successfully revamping a stagnant cybersecurity program. The strategy is the path from your “current state” to where you want to be—the “strategic objective”. Reaching the desired future state [...]
Best Practices to Secure Your Organization
The current cyber threat landscape places business at a constant state of alarm. Businesses find themselves in a non-stop battle against viruses, Trojans, and hackers, some of which aim at stealing valuable intellectual property, while others just wreak havoc [...]
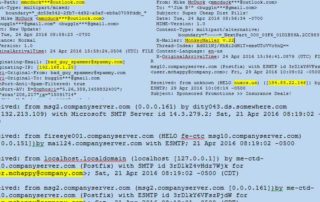
Email Headers: What can they tell the forensic investigator?
Email headers contain important information about the origin and path an email took before arriving at its final destination, including the sender’s IP address, internet service provider, email client, and even location. The information could be used to block [...]
Coffee With An Intern: John M
I’ve been interning with Alӯn, Inc. for a little over 6 months and am currently focusing in Digital Forensics. After sharing some of my career goals with a friend, he mentioned that he knew of a company worth reaching [...]